Nighthawk is an advanced toolkit of redteam tooling built with operational security in mind, including an evasive command-and-control framework. The Nighthawk beacon is highly evasive and designed to evade the modern security controls seen in mature, highly monitored environments. Nighthawk’s features are backed by MDSec’s world class research and development team, providing cutting edge capabilities not published or weaponised in the public domain. The framework provides capabilities across the toolchain, from initial access, through persistence, lateral movement and objectives.
Features
Nighthawk’s regularly expanding toolkit provides an effective framework for post-exploitation, including:
- Harnesses for secure execution of PEs, Beacon Object Files (BOFs) and .NET assemblies,
- Hidden desktop to interact with a target’s system,
- C# and Python APIs for event registration and beacon automation,
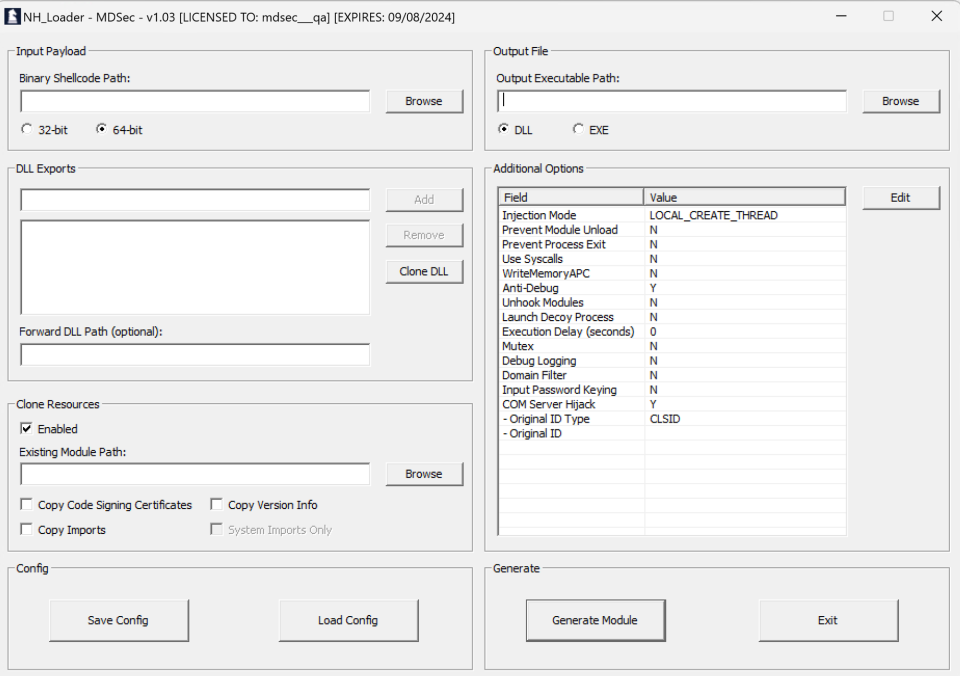
- A payload generator to create OpSec safe PE binaries such as DLL, EXEs, Service EXEs, XLLs and CPLs,
- Steganography based stager for embedding shellcode inside images,
- Built-in, configurable evasion including unhooking, indirect syscalls, stack masking, sleep obfuscation, heap encryption and more…
Highly malleable, configurable agents with custom egress and peer-to-peer comms:

Payload generators for point-and-click OpSec artifacts:
Stegonography shellcode generation tools for covert staging:
