Nighthawk 0.3 – Automate All The Things

Introduction
OpSec and evasion are two of the most important factors for red team success in modern day operations, and Nighthawk continues to lead the way in innovation on this front. However, they are not the only considerations that contribute to the overall success of an operation. The capability to streamline your workflow and extend red team tooling beyond the core beacon goes a long way in improving the efficiency and accuracy, adaptability, and collaboration of your team.
Nighthawk’s 0.3 release is probably the most significant and impactful change to the framework since its creation and almost no new beacon features or evasion strategies have been introduced. Users need not worry though, we have something exciting coming on that front…
Redesign
The key focus for this release was improving automation and operator quality of life, and to accommodate this it meant several significant architectural changes to the solution. This included a complete rewrite of the backend API server and partial but significant rewrite of the user interface.
With our 0.3 release we made several core changes to the overall product architecture, including:
- Redevelopment of the backend API server, moving from python to .NET core,
- Creation of new JSON web service APIs to expose all beacon management, alongside event registration,
- Repositioning of all c2 logic to the new API server,
- Transition of UI and API communications to web sockets,
- Creation of new modes for c2 and API server IPC, including HTTP/2 and shared sockets.
- The redesign brings a number of benefits to our users, particularly around automation and performance. To streamline interaction with our new JSON API, we also provide a number of c# helper interfaces, allowing new projects to be built with just a few lines of code.
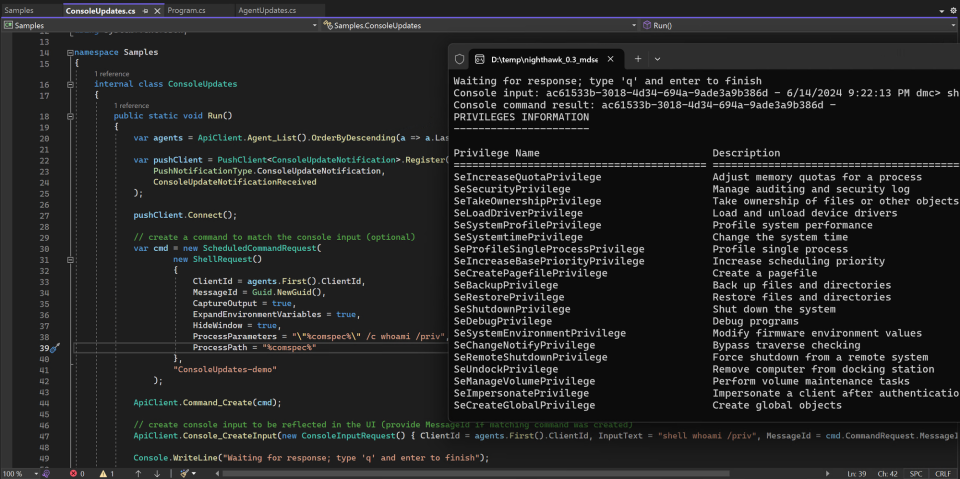
These interfaces provide full programmatic management and interactivity with the beacon; for example in a handful of lines of c#, we can create a tool to schedule new beacon commands (in this case just a shell command) and real time stream console output back:
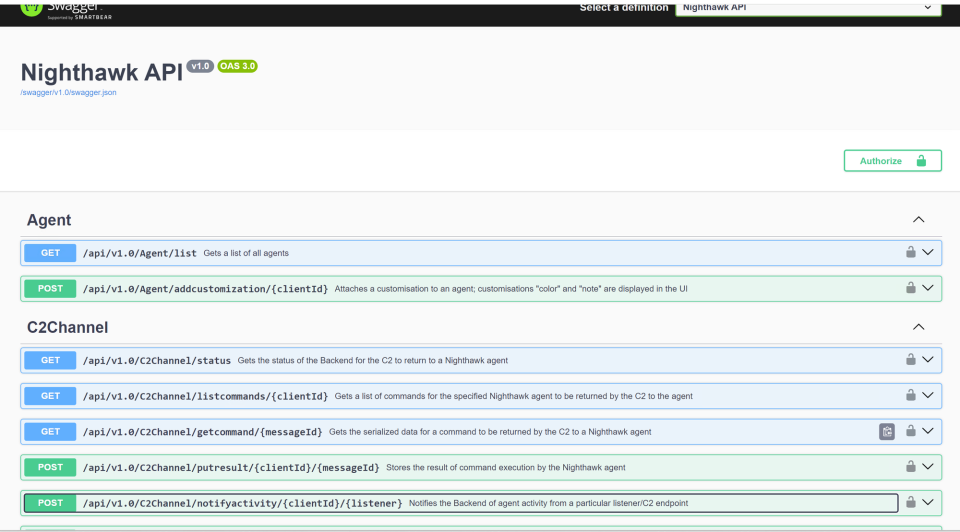
The APIs comes complete with documentation for Swagger and Redoc, with full examples of the underlying requests:
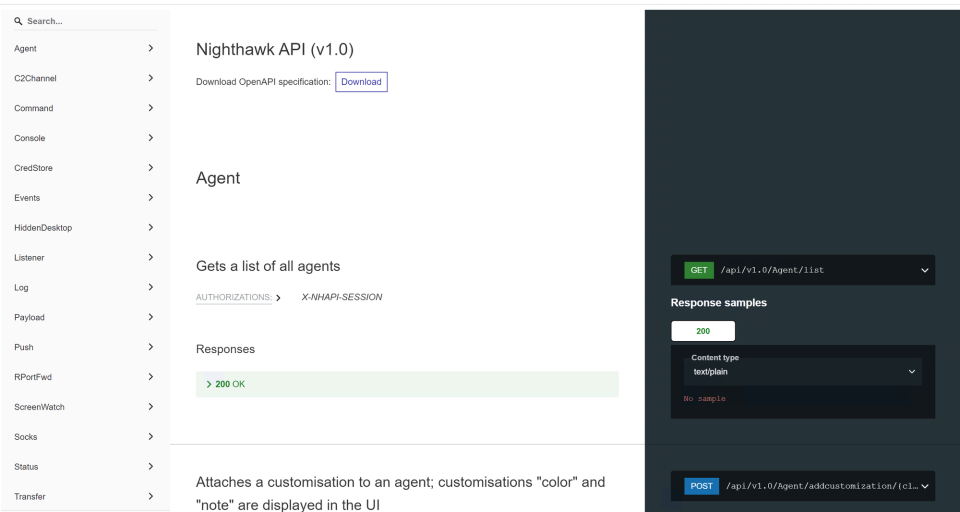
The possibilities of where you can take this are endless, but some ideas we’ve already started building out are:
- Notification bots for Slack and Mattermost,
- Bots to run post-ex tooling to automatically triage and if required, deploy persistence on endpoints following initial check-in,
- Bots to monitor virus total for hashes of any uploaded artifacts.
SOCKS Rewrite
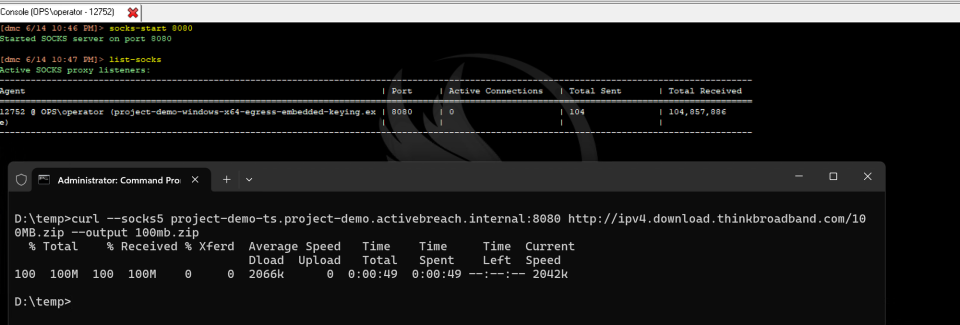
Our 0.2 SOCKS implementation was SOCKS4a and a little clunky, which we recognised as one of the key user pain points. Therefore while implementing a new backend, we also took the opportunity to completely rewrite and update our SOCKS implementation. With Nighthawk 0.3, we now offer a new, lightning fast SOCKS5 implementation with both DNS and UDP support, as well as HTTP keep alive.
Below we can see we’re easily able to get downloads in excess of 2mb/s using a 100mb test file, downloaded over the Fastly CDN redirecting to AWS and accessed over Tailscale:
Improved User Interface
One of the other key changes we made with this release was stripping back the Nighthawk user interface. Thanks to the new JSON API, we were able to rewrite the operator UI to act as a simple, thin wrapper for rendering JSON responses over web sockets, void of any logic or heavy lifting. The primary benefit of this is the significant performance increase that it brings, greatly improving the overall look and feel of the product to operators.
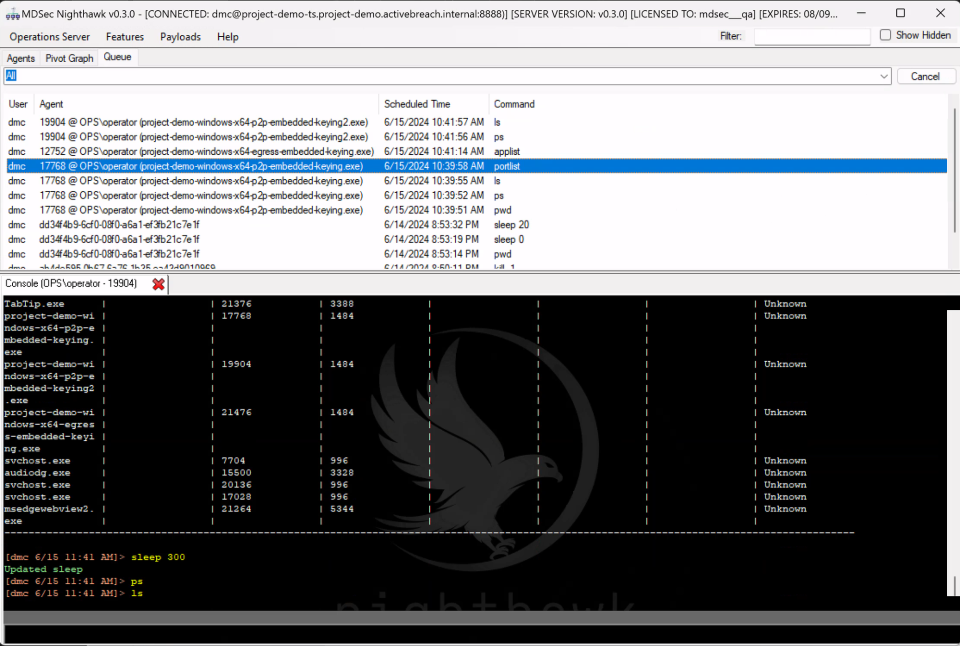
While rewriting the UI, we also introduced several new key features, including a c2 mesh graph and a modifiable beacon command queue.
Resizable console and pivot graph windows, with moveable pivot nodes make the look and feel of the UI much slicker and responsive:

We also added a visual command queue to list what pending commands are there for each agent, with the option to trivially cancel them prior to execution if you’ve made a mistake:
NHLoader
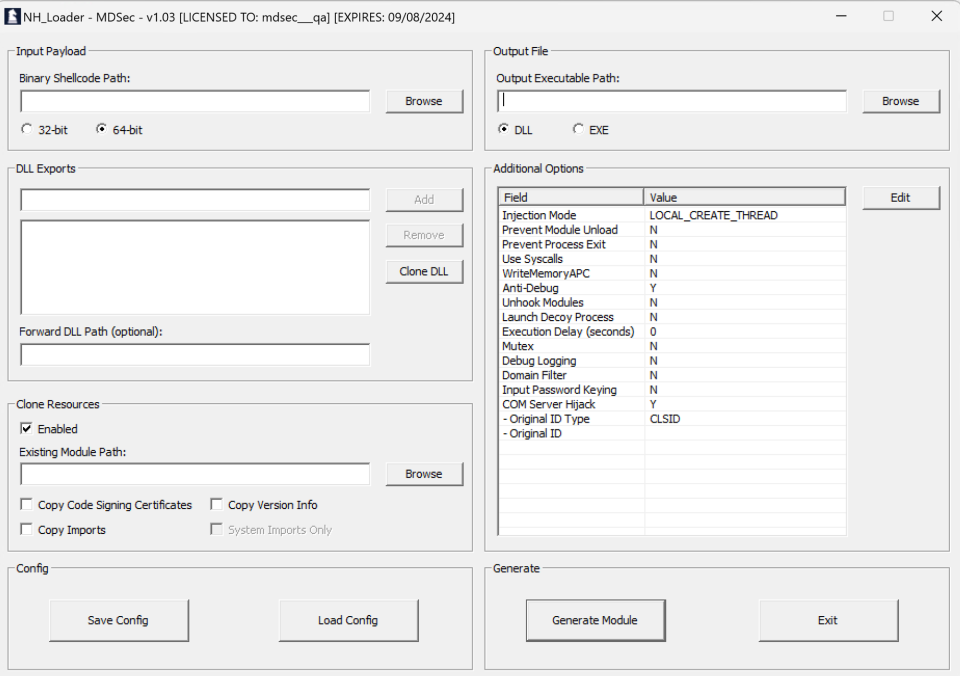
In addition to improvements to the core command-and-control component of Nighthawk, we also introduced a number of new features and improvements to NHLoader, the Nighthawk PE generator. These included the following:
A new PE infection injection mode to process legitimate PE binaries and modify them to run arbitrary shellcode on execution. This of course offers a number of benefits, borrowing the feeling of legitimacy from the original artifact, which can assist in evading certain EDR’s PE repudiation and machine learning detections. A new DLL proxying mode to support proxying to the legitimate COM server while performing COM hijacking, helping maintain the stability and integrity of the hijacked process. All of this is wrapped up in to a nice offline, point and click GUI based application:
Stego Loader
The Stego staging tool was previously built in to the main Nighthawk UI but with the 0.3 release we’ve separated it off to an offline, standalone GUI based tool.
This release also came with several new improvements to the stego tool, including timer based execution intervals and alternate modes for steganography.

Wrapping up, Nighthawk 0.3 is a significant overhaul of the product and will enable a number of new and exciting improvements we have on our roadmap for opening up more control of the platform and the beacon to our users.
Over the next few weeks, we’ll be releasing a handful of video demos illustrating the power that the new API brings to our users, so stay tuned.